OpenShift Pipelines (Tekton) - Triggers with a cup of Gitea - Cluster Setup
Set Up The Cluster Resources
Before we create an application and CI/CD resources for it, we need to setup and configure some resources:
-
Install a Gitea server
-
Set up our OpenShift cluster to trust the TLS cert on Routes
-
Configure Gitea organization and teams for this demo
-
Install a Tekton Interceptor for Gitea
Install a Gitea server to be our SCM for this demo
In resources that you cloned I have provided a demo Deployment of Gitea for us to use. Check out Gitea here: https://gitea.io/en-us/
Let’s install that first. Note: This assumes that you are using Code Ready Containers. If you are not, then you will need to modify the PersistentVolumeClaim in this YAML file.
-
Create a Namespace for the Gitea server:
oc new-project gitea -
Create the Gitea server:
oc apply -f ~/tekton-tutorial/gitea-demo/gitea-server.yaml -n gitea -
Create a edge terminated TLS route for Gitea
oc create route edge gitea --service=gitea-http -n gitea
Trust the Cluster Cert on the Gitea Route
-
Grab the self-signed certificate from the Gitea Route:
ROUTE_CERT=$(openssl s_client -showcerts -connect $(oc get route gitea -o=jsonpath='{.spec.host}' -n gitea):443 </dev/null 2>/dev/null|openssl x509 -outform PEM | while read line; do echo " $line"; done) -
Create a ConfigMap in the
openshift-confignamespacecat << EOF | oc apply -n openshift-config -f - apiVersion: v1 kind: ConfigMap metadata: name: demo-ca data: ca-bundle.crt: | # CRC Route Cert ${ROUTE_CERT} EOF -
Patch the default Proxy instance for the OpenShift cluster:
Note: This will cause Code Ready Containers to stop. In a real cluster this would be a rolling restart of your nodes.
oc patch proxy cluster --type=merge --patch '{"spec":{"trustedCA":{"name":"demo-ca"}}}' -
Wait for Code Ready Containers to shutdown:
Run the following command:
crc statusWait until it indicates that the CRC VM has stopped.
CRC VM: Stopped OpenShift: Stopped (v4.10.9) Podman: Disk Usage: 0B of 0B (Inside the CRC VM) Cache Usage: 17.6GB Cache Directory: /Users/charrogruver/.crc/cache -
Restart Code Ready Containers:
crc start
Configure Gitea
-
Log into your Gitea server:
Get the URL for the Gitea route:
echo "https://$(oc get route gitea -o=jsonpath='{.spec.host}' -n gitea)"Copy that URL into your browser and log into the Gitea server.
Note: The initial admin user credentials are:
User Name: giteaPassword: passwordYou will be prompted to change the admin user’s password.
Note: You also have a developer user,
developerwho’s initial password is alsopassword. -
Select
Site Administrationfrom the drop down menu in the top right corner:
-
Select User Accounts:
-
Create a Service Account for our demo:
-
Update the service account by unchecking
May Create Organizations
-
Go back to
Site Administrationand selectOrganizations:
-
Create an Organization for the demo code:
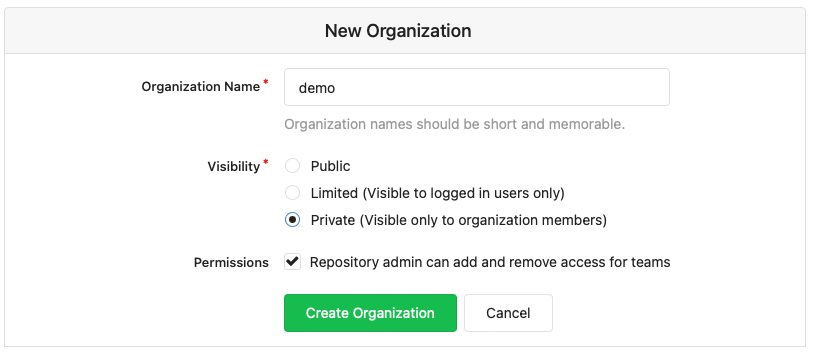
-
From the new Organization, select
View Demoon the right hand side of the screen: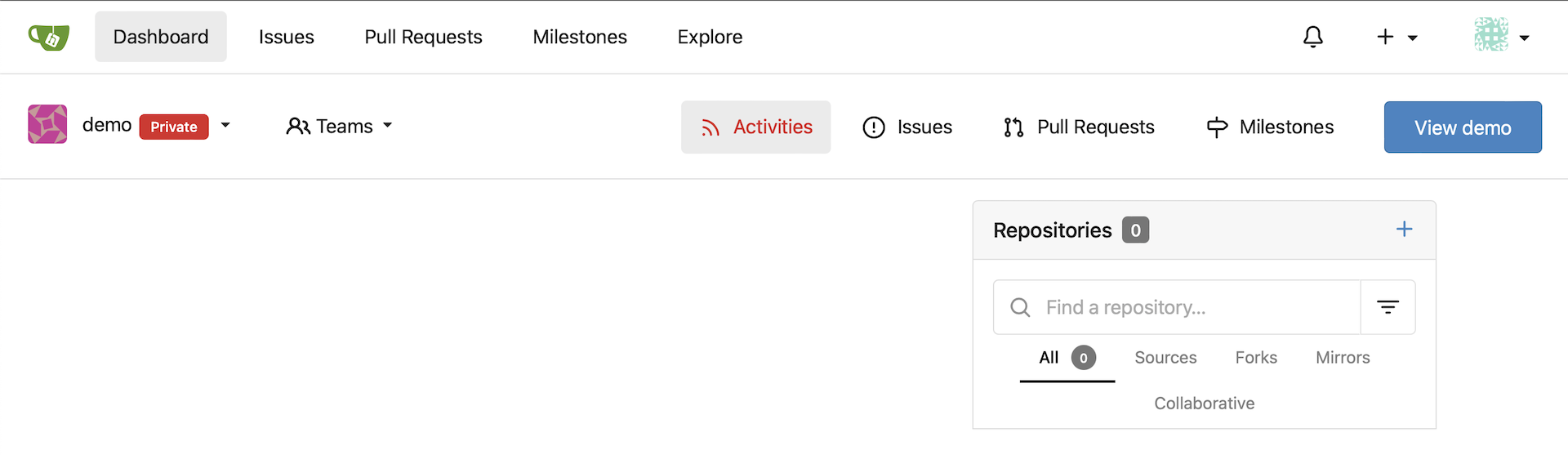
-
From the new Organization, select the
OwnersTeam from theTeamsmenu on the right hand of the screen: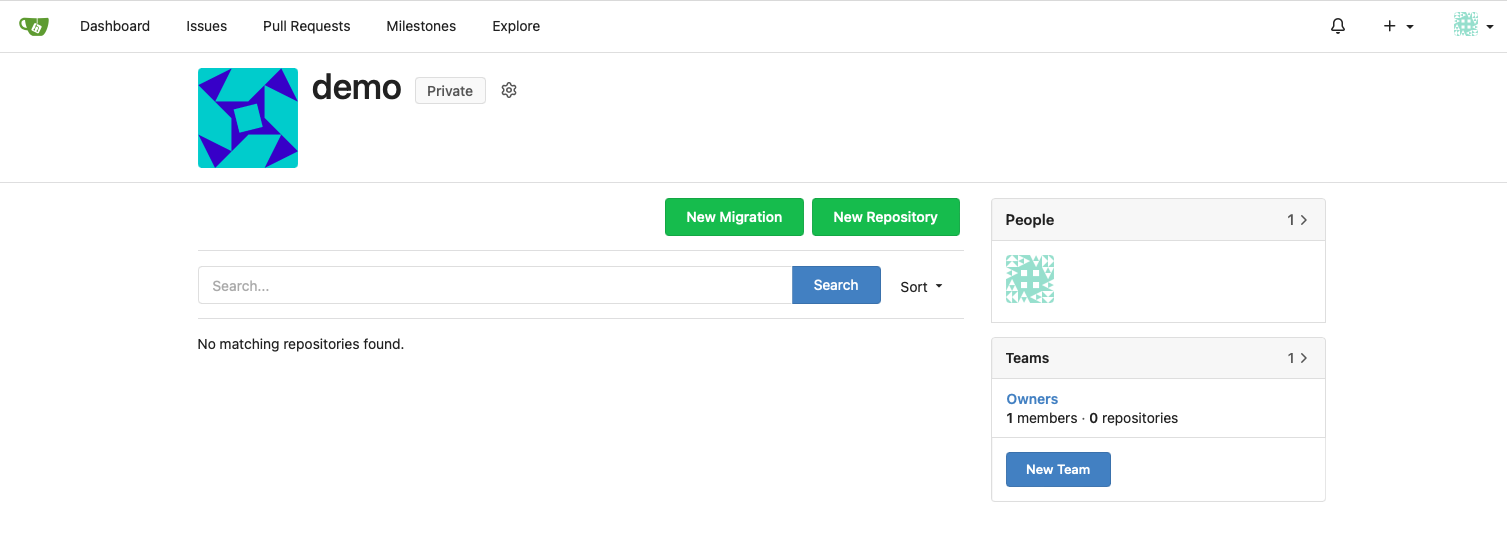
-
Add your
developeraccount as a Team member: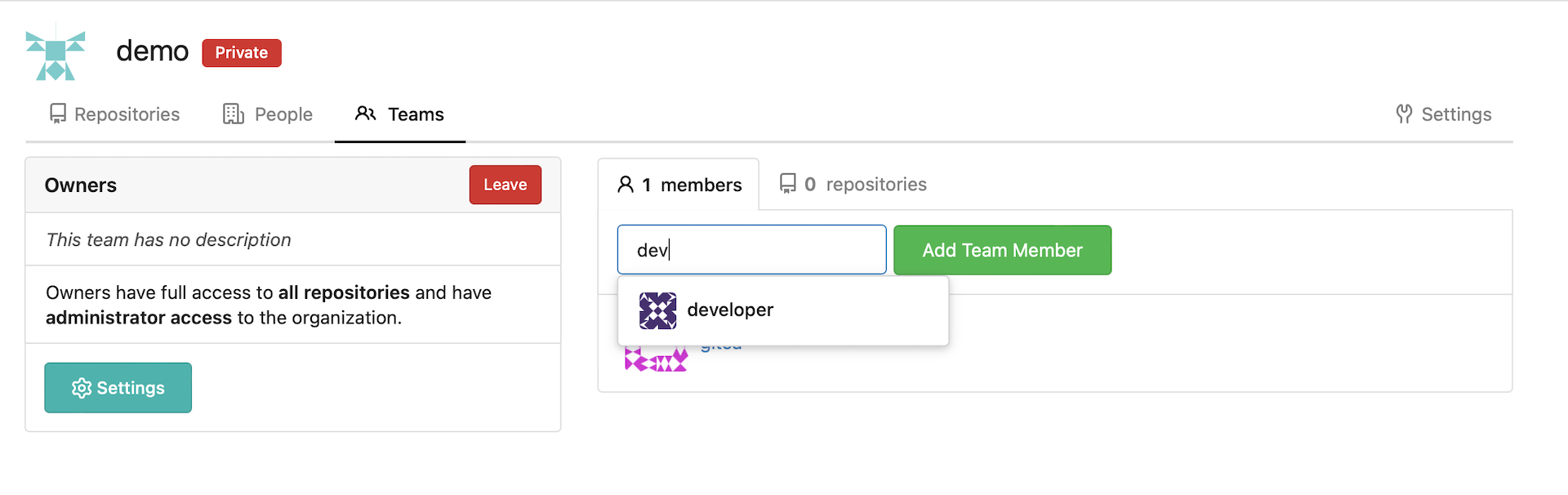
-
Go back to the
demoOrganization and this time selectNew Teamfrom the right hand menu:Create a team as shown for the demo service account:
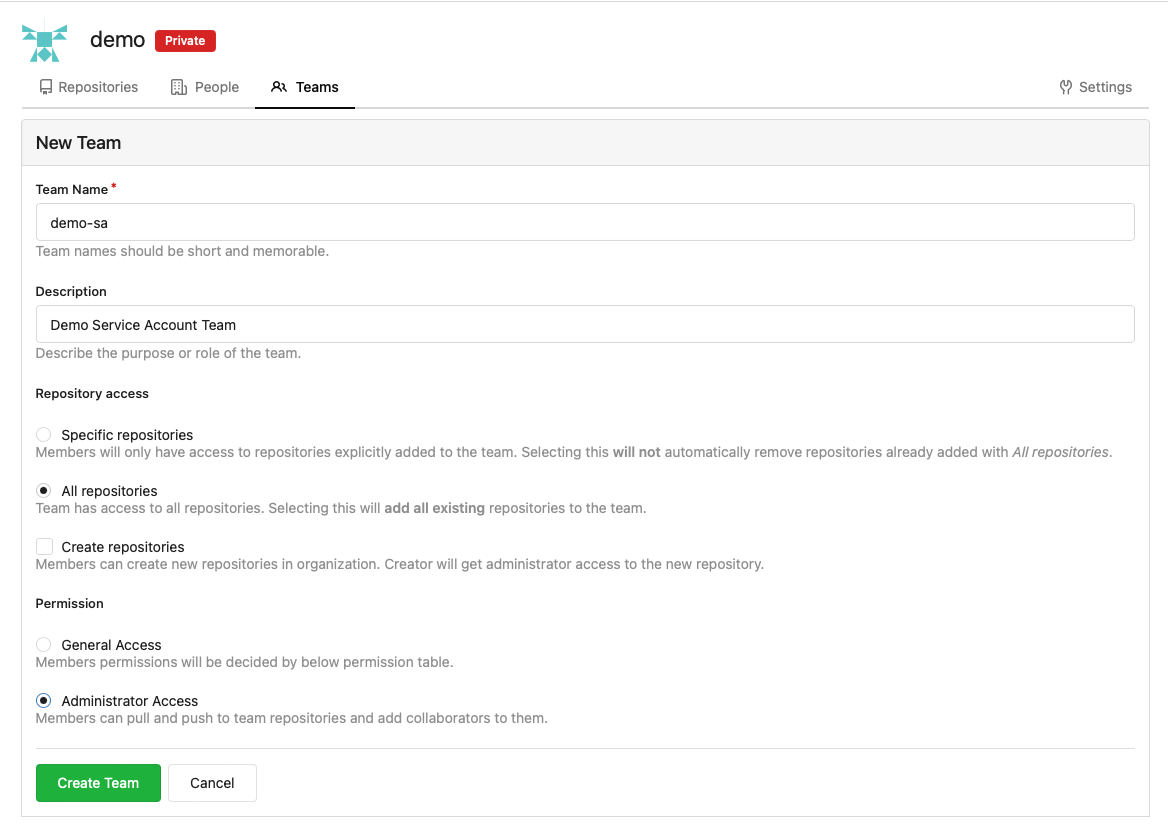
-
Go back to the
demoOrganization and select the newdemo-saTeam from the right hand menu: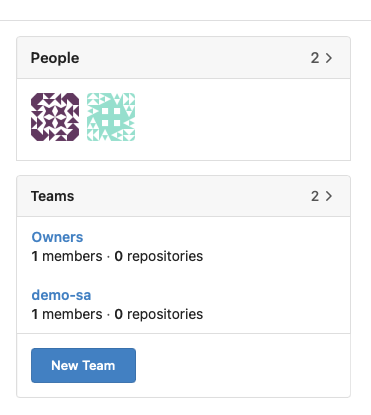
-
Add the
demo-sauser to the Team: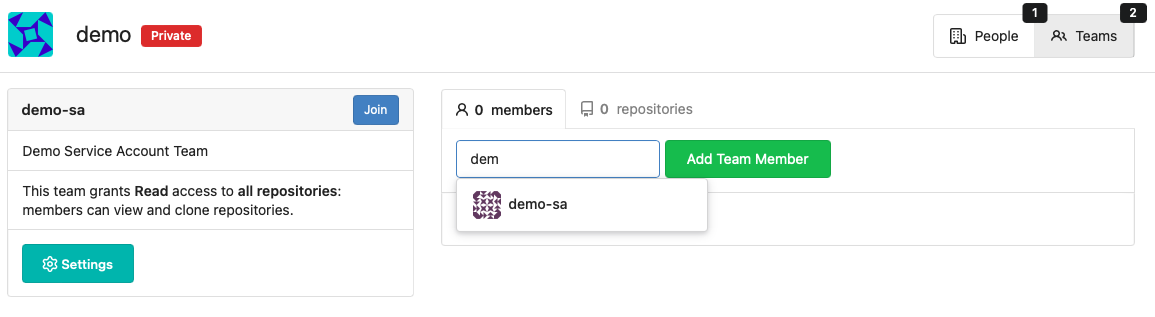
-
Logout of Gitea.
Create Credentials For Your Gitea developer Account
-
Log into the Gitea server with the userid
developerand passwordpassword
-
You will be prompted to create a new password:
Install the Gitea Tekton Interceptor:
-
Note: You will need to be logged in as a cluster administrator for this step.
If you are using CRC then do this:
crc console --credentialsUse the password in the output to log into the cluster:
crc login -u kubeadmin https://api.crc.testing:6443 -
Create the Interceptor:
oc apply -f ~/tekton-tutorial/gitea-demo/gitea-interceptor.yaml -n openshift-pipelines -
Create a edge terminated TLS route for the Interceptor:
oc create route edge gitea-interceptor --service=gitea-interceptor -n openshift-pipelines
Note: If you are curious, the code for the Interceptor is here: https://github.com/cgruver/gitea-interceptor
Install The Pipeline Resources
Note: You will need to be logged in as a cluster administrator for this step.
-
Install the provided Templates into the
openshiftnamespace:oc apply -f ~/tekton-tutorial/gitea-demo/pipeline-manifests/templates/ -
Install the ClusterTasks:
oc apply -f ~/tekton-tutorial/gitea-demo/pipeline-manifests/clusterTasks/
Now, let’s create a Quarkus application and deploy it!
OpenShift Pipelines (Tekton) - Triggers with a cup of Gitea - Quarkus Demo