Lab Network Configuration
Note: This is part of a series. Make sure you started here: Building a Portable Kubernetes Home Lab with OpenShift - OKD4
All of these devices will be running the OpenWRT linux distribution. Find out more here: https://openwrt.org
Note: If at any time you need to reset the router, or any of the below commands fail and need to be rerun, do this:
Hold the highlighted button for about 10 seconds. When you first press the button, the left most LED will start to slowly blink. After about 3-4 seconds it will blink a bit faster. After about 9-10 seconds it will blink really fast. At this point, let go of the button. Your router will factory reset itself.

Configure the Edge Router
-
Connect to your edge router:
Note: The
GL-MV1000Wis not currently available, (06-2022), so you will either need to use aGL-MV1000, and set up your own lab wifi with a separate access point, or you can use theGL-AR750S.- Do not connect your router to any other network devices yet.
- Power it on and connect to it from your workstation.
- With the
GL-MV1000WorGL-AR750Syou can connect to the WiFi. The initial SSID and passphrase are on the back of the router. Otherwise, connect from your workstation with a network cable. I generally use a network cable to apply the initial configuration to all of my GL.iNet routers, wireless or not. - Ensure that you can ping the router:
ping 192.168.8.1
-
Initialize the router configuration:
You can use the GL.iNet
GL-MV1000WorGL-AR750Seither as an access point, or as an access point plus repeater for wireless connection to your home network.I highly recommend using a cable to connect the router to your home network. You will get much faster network speeds than you get in repeater mode. But, the repeater mode is usable. Especially when traveling.
To use the router with a wired connection to your home network, do this:
labcli --router -i -e -wlYou will prompted to enter an
ESSIDand a passphrase for your new lab network.To use the router in repeater mode, do this instead:
labcli --router -i -e -wl -wwYou will prompted to enter the
ESSID,Channel, andPassphrasefor the wireless network you are bridging to, and you will prompted to enter anESSIDand a passphrase for your new lab network.Note: The router will dump a list of the Wireless Networks that it sees. You can get the channel from that list as well.
When the configuration is complete, the router will reboot.
-
Finish configuring the router:
Now, connect the router to your home network if you are not using the wireless-repeater mode.
At this point you should be able to connect your workstation to your new lab WiFi network.
Finish the configuration:
labcli --router -s -eNote: If you want to see the details of what labcli scripts are doing, I have a page with the manual instructions here: Edge Network Router Configuration
-
Wait for the router to reboot, and then reconnect to your new lab network.
-
Verify that DNS is working properly:
ping google.com
Configure the Internal Network Router
This configuration is very similar to setting up the edge router.
-
Connect to your internal network router:
Do not connect your router to any other network devices yet.
Power it on and connect to it from your workstation with a network cable.
Ensure that you can ping the router:
ping 192.168.8.1 -
Initialize the router configuration:
labcli --router -i -d=devWhen the configuration is complete, the router will reboot.
-
Finish the router configuration:
Connect the internal router WAN port to one of the two LAN ports on the edge router.
The WAN port is the left most port.
Ensure that you can connect to the router:
labctx dev ping ${DOMAIN_ROUTER}Now, complete the router configuration:
labcli --router -s -d=devWhen the configuration is complete, the router will reboot.
Note: If you want to see the details of what labcli scripts are doing, I have a page with the manual instructions here: Internal Network Router Configuration
Configure the Raspberry Pi
We are going to use the edge router that we set up previously to configure the OS for the Raspberry Pi.
Note: If you are using the GL-AR750S, you will need a USB type A thumb drive with at least 2-GB capacity. The thumb drive will be reformatted during this process, so don’t use one with important files on it.
-
Insert the SD Card into the edge router.
-
If you are using the
GL-AR750S, insert the thumb drive into the USB slot. -
Install and configure OpenWRT on the SD Card:
labcli --pi -iThis will take a while to complete.
-
Remove the SD Card from the edge router and insert it into the Pi.
-
If you are using the
GL-AR750S, remove the thumb drive from the USB slot. -
Connect the network adapter from the Pi to the other LAN port on the edge router.
-
Power on the Pi.
-
Ensure that the Pi is on line:
ping bastion.my.awesome.lab -
Complete the configuration of the Pi:
labcli --pi -sWhen the configuration is complete, the Pi will reboot.
Install Developer Tools
-
Install Sonatype Nexus
labcli --dev-tools -nNote: If you want to see the details of what labcli scripts are doing, I have pages with the manual instructions here:
-
Start Nexus
ssh root@bastion.my.awesome.lab "/etc/init.d/nexus start" -
Nexus will take a while to start for the first time.
Go make a nice cup of tea, coffee, or hot beverage of your choice. Nexus will be up shortly.
-
After Nexus has started, trust the new Nexus cert on your workstation:
labcli --trust -n -
Install Gitea
labcli --dev-tools -gNote: If you want to see the details of what labcli scripts are doing, I have pages with the manual instructions here:
-
Start Gitea
ssh root@bastion.my.awesome.lab "/etc/init.d/gitea start" -
Trust the gitea certs on your workstation:
labcli --trust -gThe Gitea web console will be at:
https://gitea.my.awesome.lab:3000The script creates two users for Gitea:
gitea- This is your Gitea admin userdevuser- This is a non-privileged user for Gitea.
Both passwords are initialized to
password. You will be prompted to change them when you log in.
Set up Nexus for image mirroring:
-
Log into Nexus:
Get the initial admin password for Nexus:
echo $(ssh root@bastion.my.awesome.lab "cat /usr/local/nexus/sonatype-work/nexus3/admin.password")Now point your browser to
https://nexus.my.awesome.lab:8443. Login, and create a password for your admin user.
If prompted to allow anonymous access, select to allow.
The ? in the top right hand corner of the Nexus screen will take you to their documentation.
-
We need to create a hosted Docker registry to hold the mirror of the OKD images that we will use to install our cluster.
-
Login as your new admin user
-
Select the gear icon from the top bar, in between a cube icon and the search dialog.
-
Select
Repositoriesfrom the left menu bar.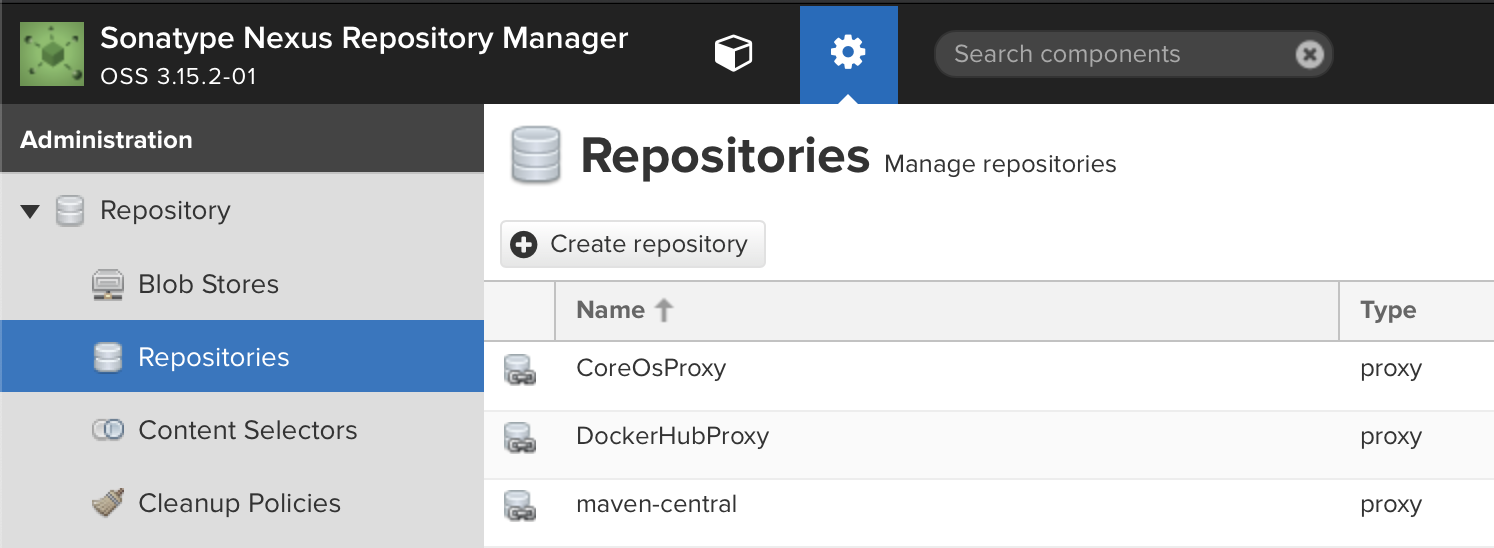
-
Select
+ Create repository -
Select
docker (hosted)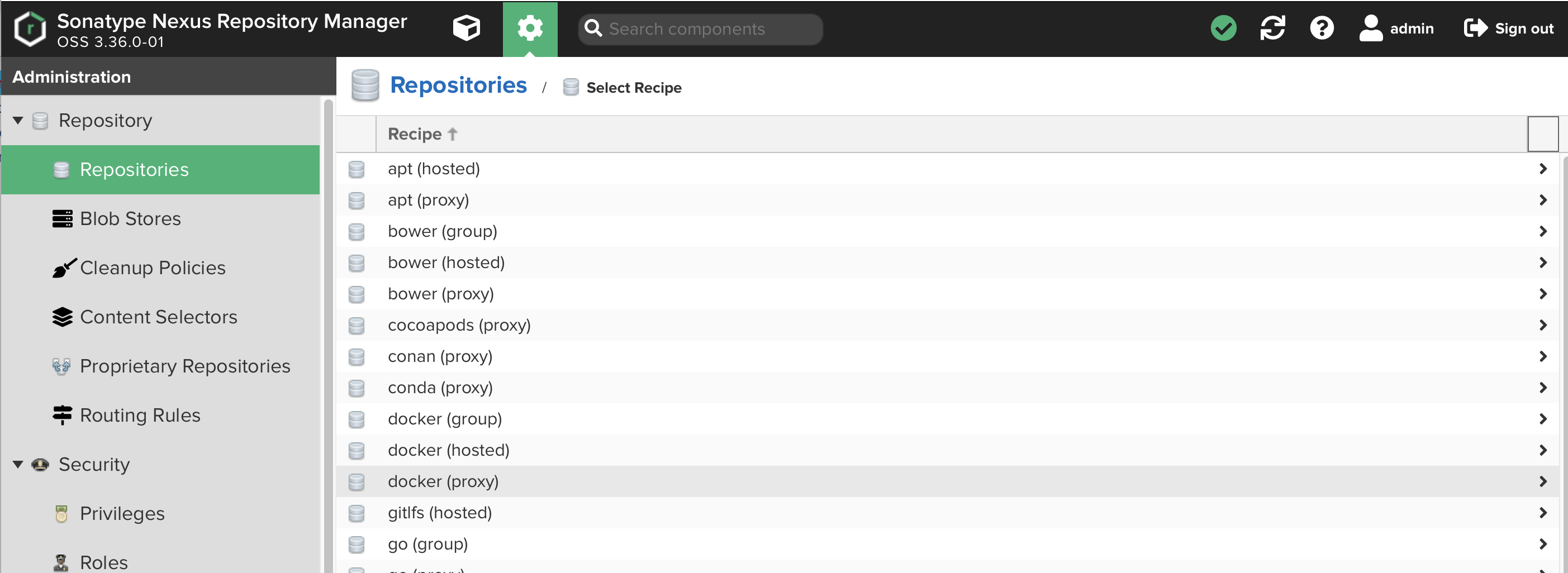
-
Name your repository
okd -
Check
HTTPSand put5001in the port dialog entry -
Check
Allow anonymous docker pull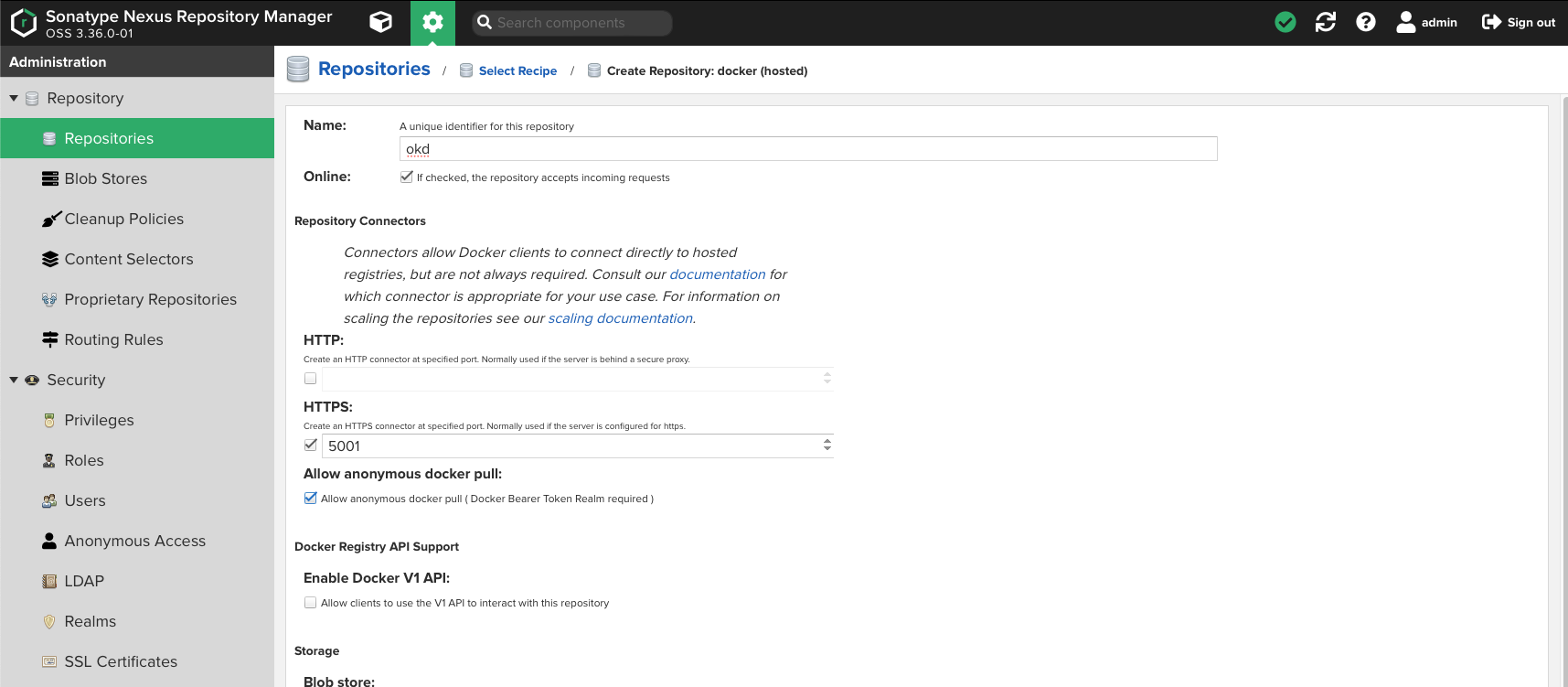
-
Click
Create repositoryat the bottom of the page.
-
-
Next we need to create a Proxy registry for
gcr.io. We’ll need this later on for Tekton.-
Select
Repositoriesfrom the left menu bar. -
Select
+ Create repository -
Select
docker (proxy) -
Name your repository
gcr-io -
Check
Allow anonymous docker pull -
Set
https://gcr.ioas theRemote storagelocation.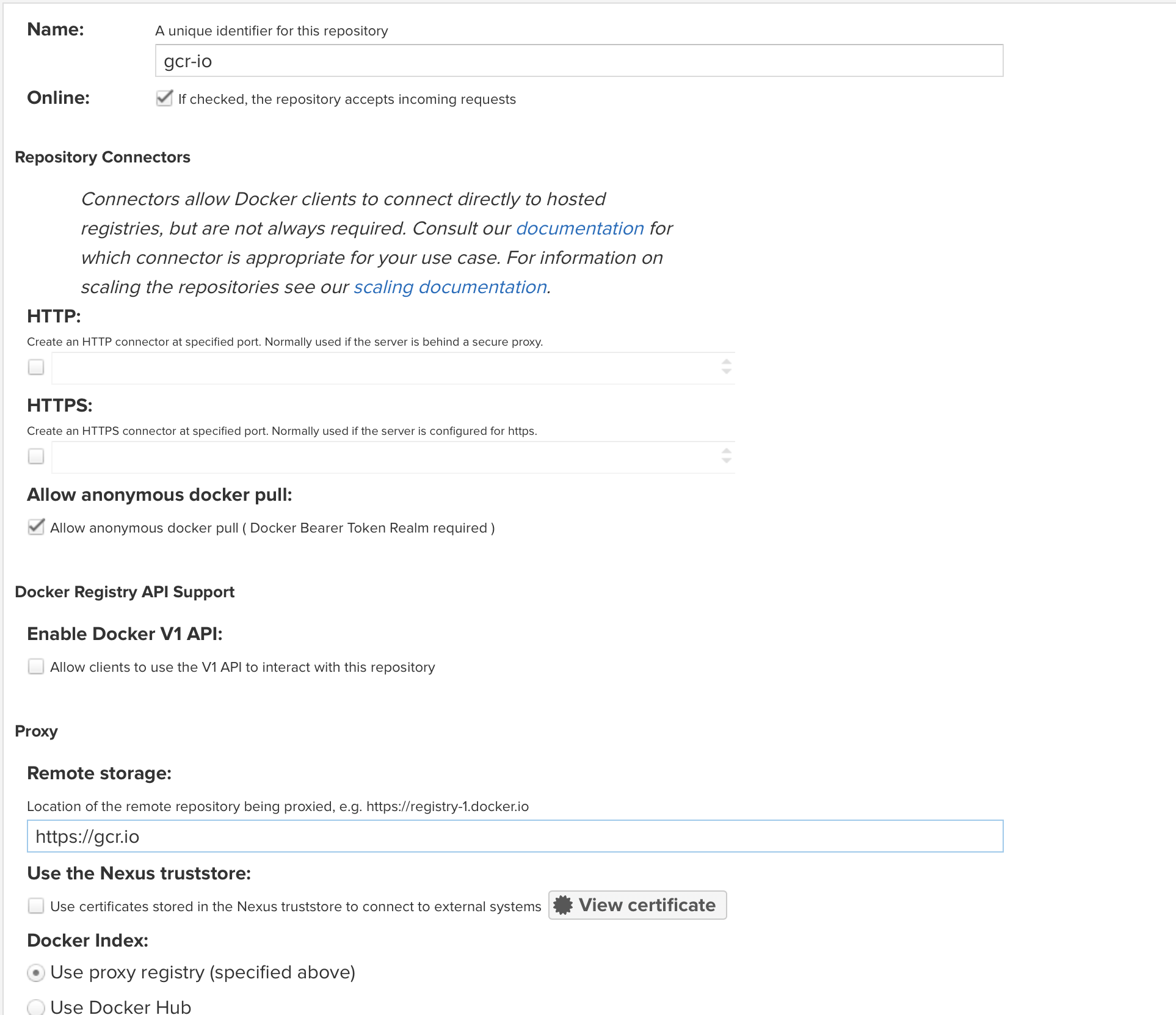
-
Click
Create repositoryat the bottom of the page.
-
-
Finally, create a Group registry as an umbrella for the hosted and proxy registries.
-
Select
Repositoriesfrom the left menu bar. -
Select
+ Create repository -
Select
docker (group) -
Name your repository
lab-registry -
Check
HTTPSand put5000in the port dialog entry -
Check
Allow anonymous docker pull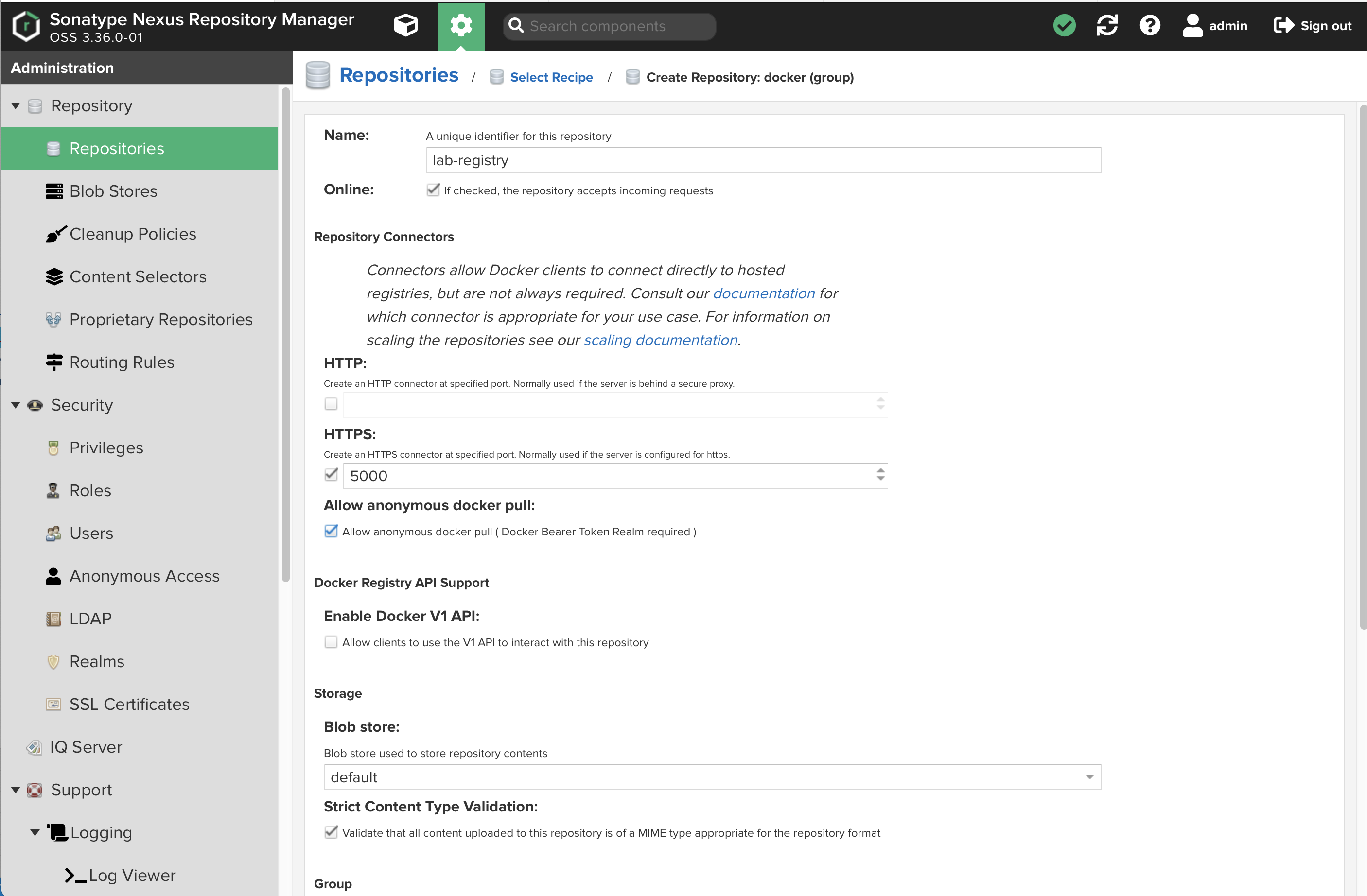
-
Add your other two registries as group members:
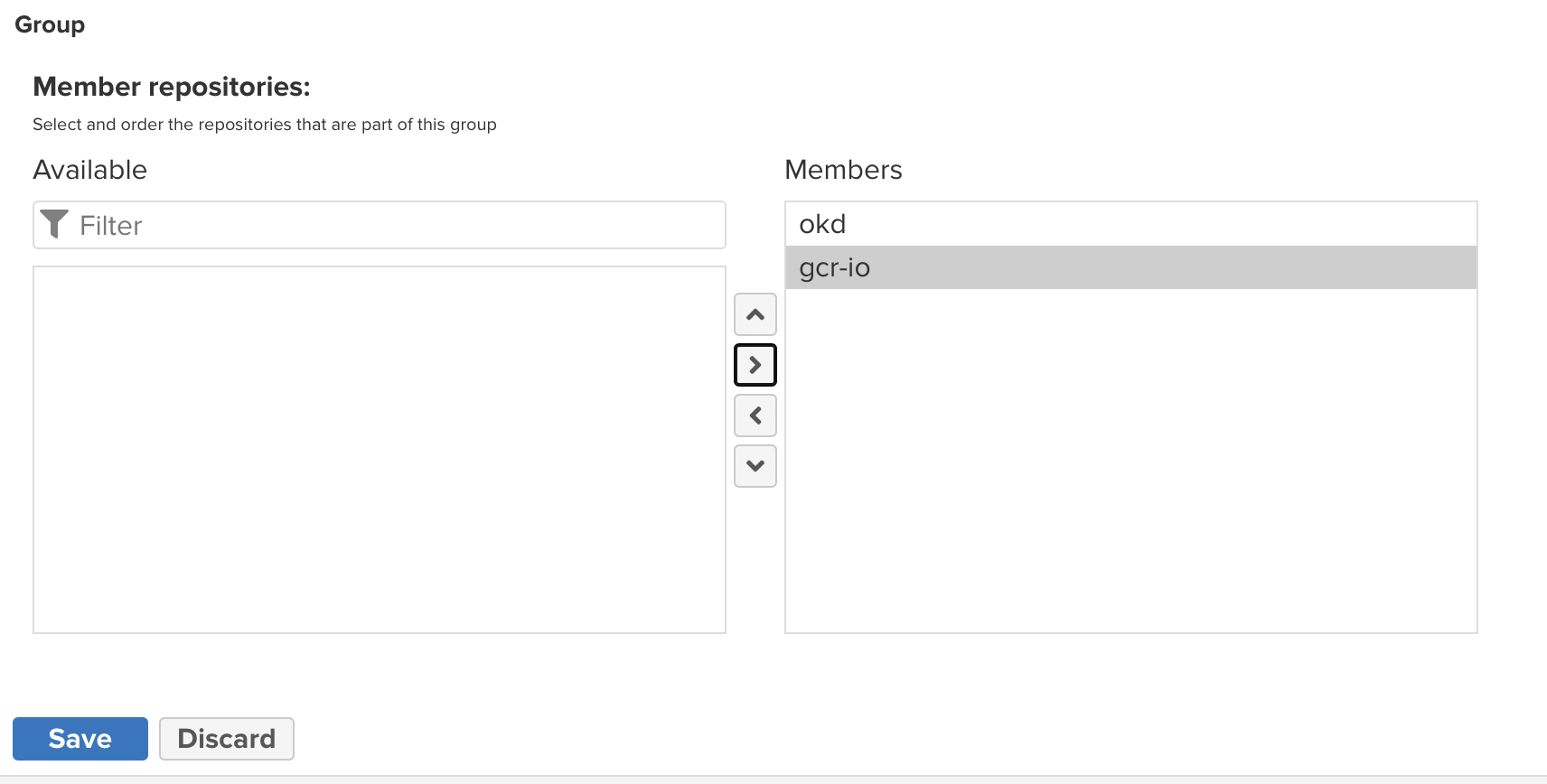
-
Click
Create repositoryat the bottom of the page.
-
-
Now expand the
Securitymenu on the left and selectRealms-
Add
Docker Bearer Token Realmto the list of activeRealms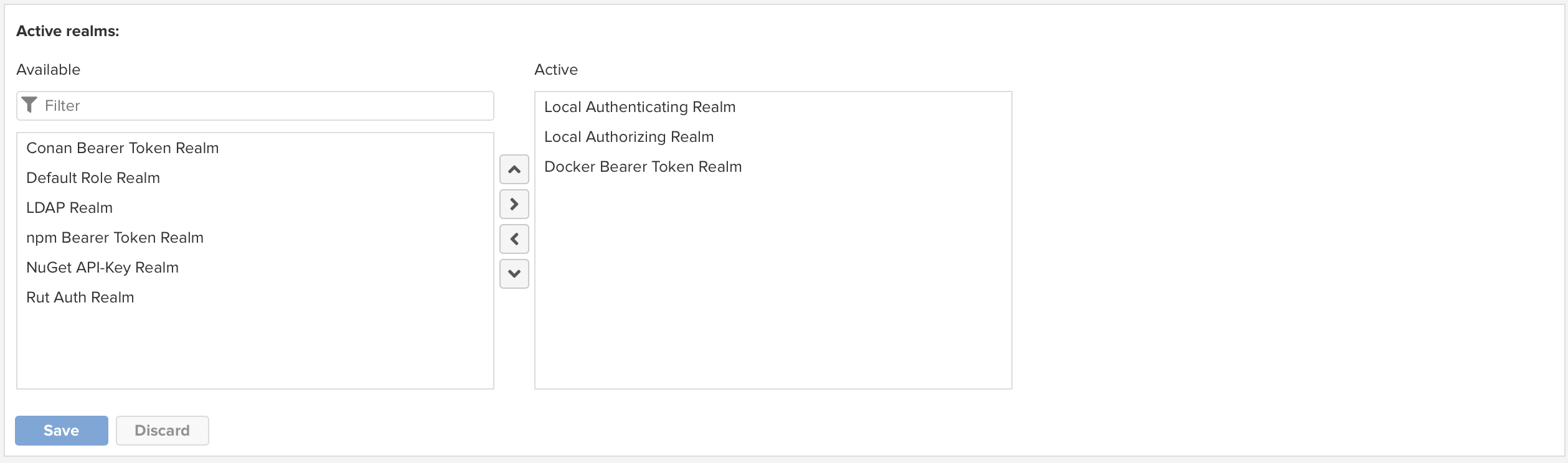
-
Click
Save
-
-
Now, select
Rolesfrom the expandedSecuritymenu on the left.-
Click
+ Create roleand selectNexus role -
Create the role as shown:
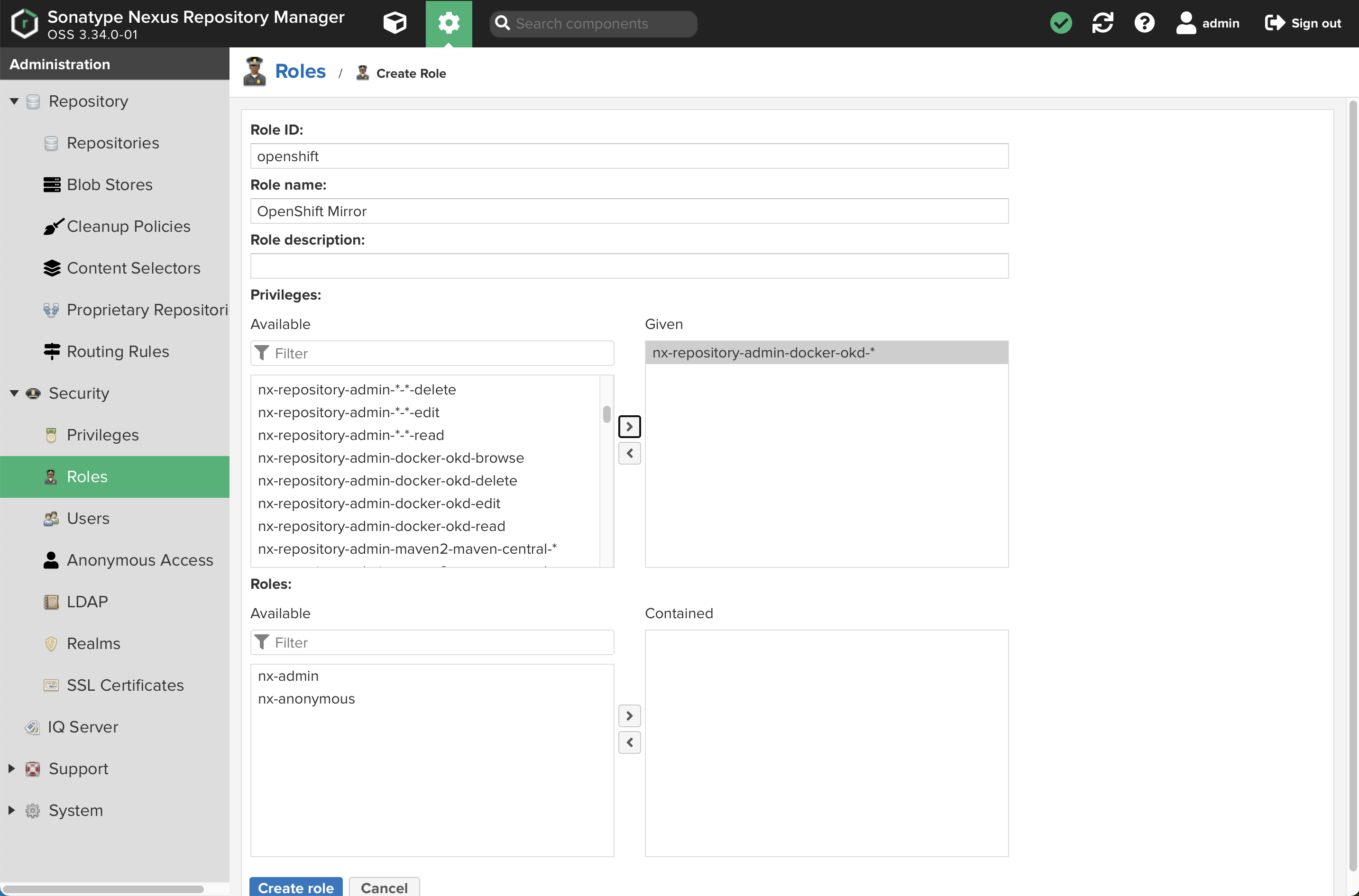
-
Add the appropriate privileges as shown:
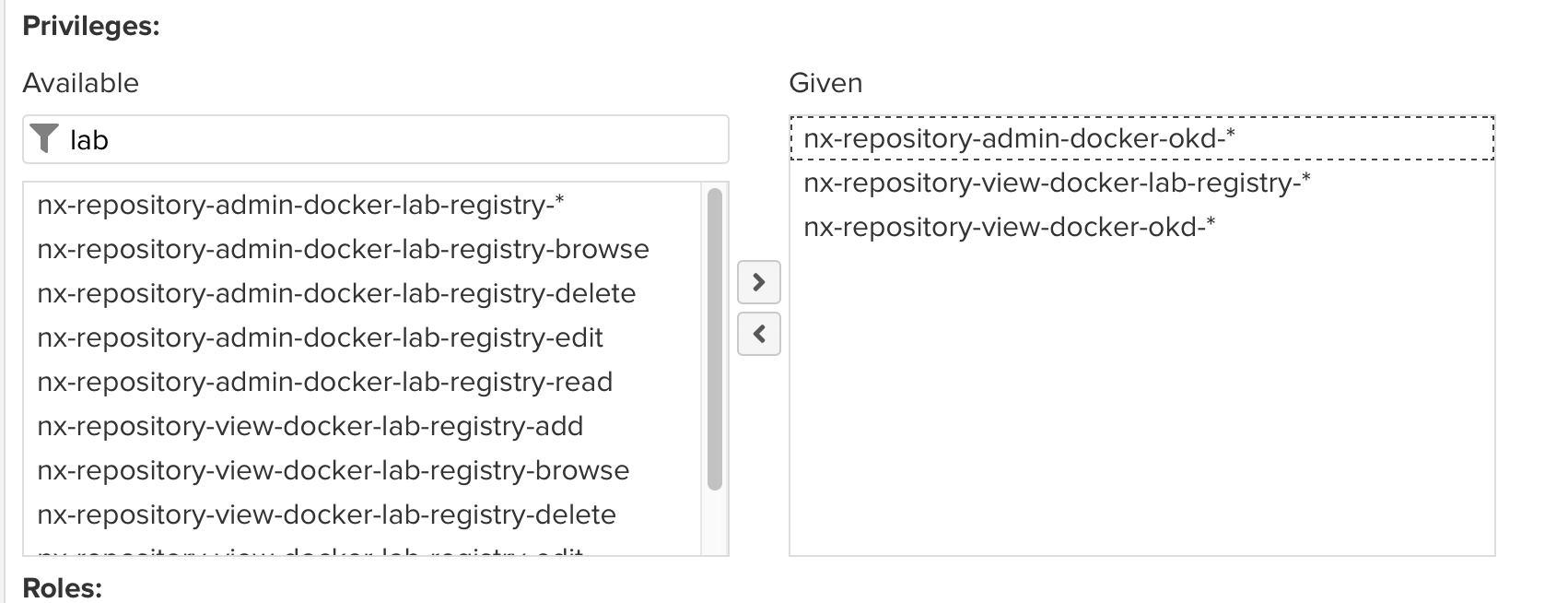
-
Click
Create role
-
-
Now, select
Usersfrom the expandedSecuritymenu on the left.
-
Click
Create local user -
Create the user as shown:
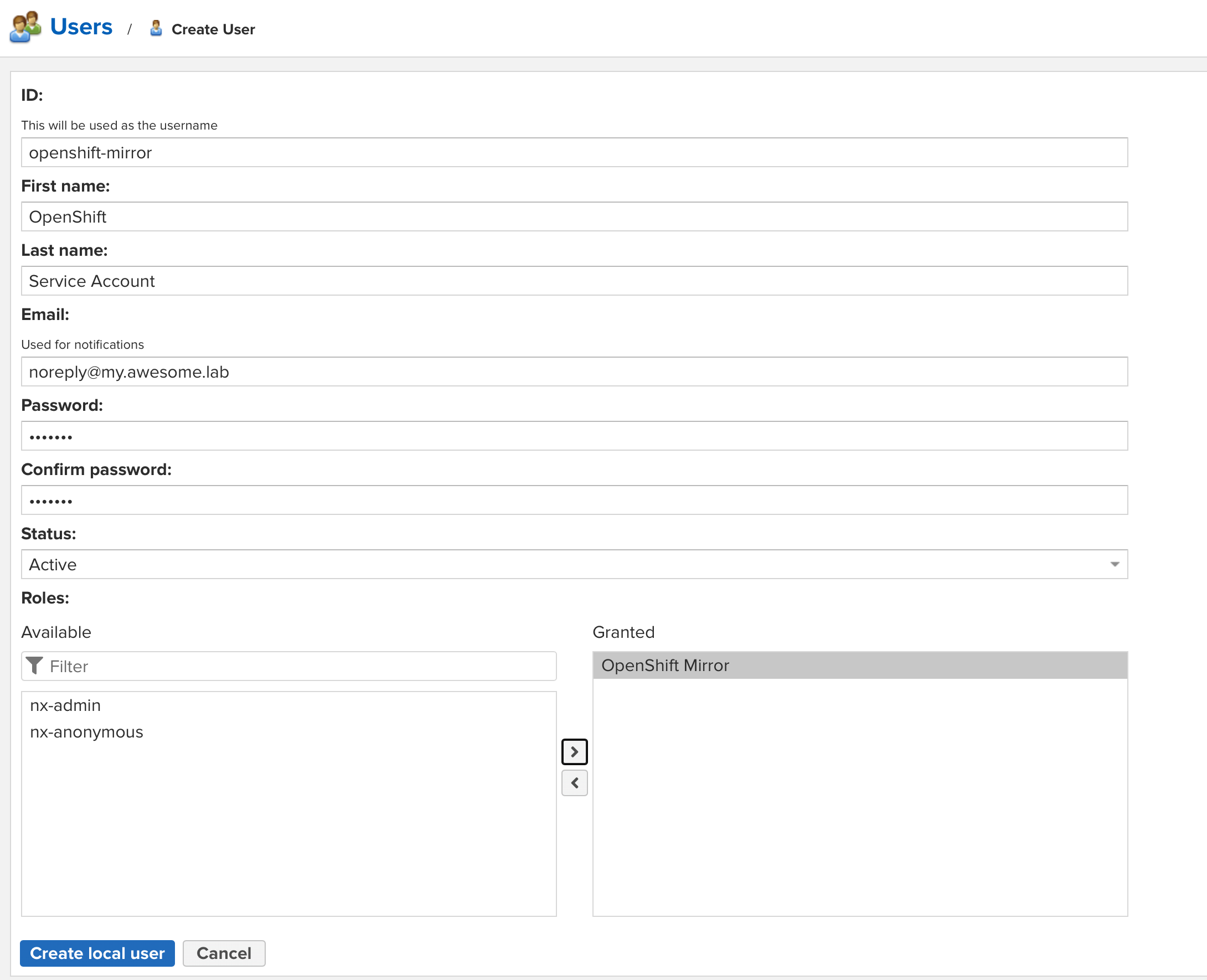
-
We’re now ready to start the installation of OpenShift.